With the
Azure AD Conditional
Access feature, rules for access to Microsoft Cloud Services and other apps
registered in Azure AD can be bound to conditions.

An example
is the rule: When accessing with an unmanaged device, the user is prompted
to use multi-factor authentication.
With the
feature "Use Conditional Access App Control" as an option in the
Session Controls area within Azure AD Conditional
Access, advanced scenarios can be setup.
Options:
- Prevent
data exfiltration
- Protect
on download
- Prevent
upload of unlabeled files
- Block
potential malware
- Monitor
user sessions for compliance
- Block
access
- Block
custom activities
Example:
- Automatically
assign a sensitivity label when a file is downloaded.
- Filter
based on regular expressions: “Include Files that match a custom expression”
- Block
Upload if Maleware is detected.
- This is can be done because the Cloud
App Security service then acts as a proxy for accessing the application:
Setup Conditional Access App Control
To register
an app, the wizard can be used in Cloud App Security via Investigate ->
Connected Apps -> Conditional Access App Control Apps. Another and much
simpler way is to use a conditional access policy as an easy start:
Azure
AD Security -> Conditional Access
New
Policy
Section
„Access controls“ -> „Session“
Use
„Use Conditional Access App Control“
Use
„Use custom policy to set an advanced policy in Cloud App Security“
The above
method works for the so called featured
apps. In order to make this option work for the Office
365 Featured Apps, Office 365 must be registered under "Connected
Apps" in Cloud App Security:
Once an app
is registered, session policies can be created that will take effect when the
app is used.
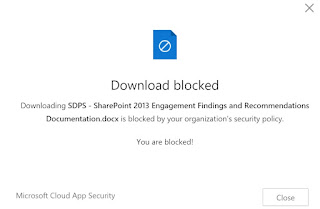
Example: If the user Oliver Hardy tries to download a
document from Microsoft Teams (SharePoint) that contains the term
"confidential", the download is blocked.Further scenarios
- Monitor / block activities based on file conditions like Classification Label, File Name, Files Size or File Extension
- Monitor / block activities like Cut/Copy Item, Paste Item, Print Item, Send Item
- Block downloads based on conditions
- Apply classification label to downloads
- Apply rules based on Maleware detection
Impact from the user's perspective
When
opening the app, the user is notified that access is monitored by Cloud App
Security. The fact that a proxy is involved can also be recognized by the URL.
This now has the addition access-control.cas.ms:
If the user
Oliver Hardy now tries to download a document he gets the following message: